- Nitrokod targeted over 111,000 users from 11 different countries.
- The crypto mining campaign attains motion in 2019 globally.
A Turkish-based entity known as Nitrokod is alleged to actively participate in a crypto mining campaign that imitates computer software for Google Translate, which has affected over 111,000 victims in around 11 countries globally since 2019.
Maya Horowitz, vice president of research at Check Point, mentioned in her interview with a news website, “Anyone can use the malicious tools” and “They cab be found by a simple web search, downloaded from a link and installation is a simple double-click.”
The peoples trapped by Nitrokod belong to several countries: The United Kingdom, The United States, Sri Lanka, Greece, Israel, Germany, Turkey, Cyprus, Australia, Mongolia, and Poland.
The campaign aimed at serving malware with the help of free software available on websites like Uptodown and Softpedia. It is an impressive strategy; the malware puts off its execution for weeks and splits its malicious movement from the fake downloaded software to evade detection.
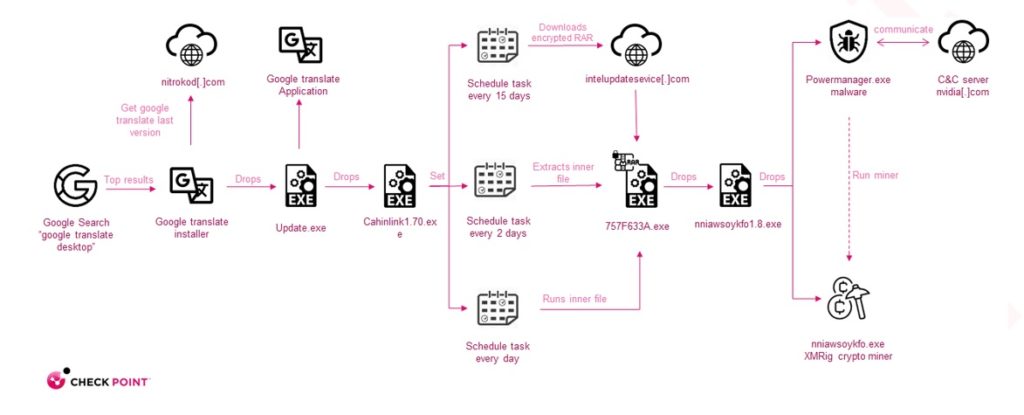
The installation process of the affected software is heeded by launching an update executable to the disk that executes in four stage attack sequence with each dropper paving for the next until the real malware is dropped in the seventh stage.
After the completion of the malware connection, remote command and control (C2) are formed to regain a configuration file to execute the coin mining activity.
A special feature of the Nitrokod campaign is that the fake software offered for free is for services that do not have an official desktop version, likewise YouTube Music, MP3 Download Manager, Yandex Translate, Microsoft Translate, and PC Auto Shutdown.
Horowitz mentioned, “What’s most interesting to me is the fact that the malicious software is so popular, yet went under the radar for so long,” and “The attacker can easily choose to alter the final payload of the attack, changing it from a crypto miner to, say, ransomware or banking trojan.”
Andrew is a blockchain developer who developed his interest in cryptocurrencies while pursuing his post-graduation major in blockchain development. He is a keen observer of details and shares his passion for writing, along with coding. His backend knowledge about blockchain helps him give a unique perspective to his writing skills, and a reliable craft at explaining the concepts such as blockchain programming, languages and token minting. He also frequently shares technical details and performance indicators of ICOs and IDOs.


 Home
Home News
News










